Overview
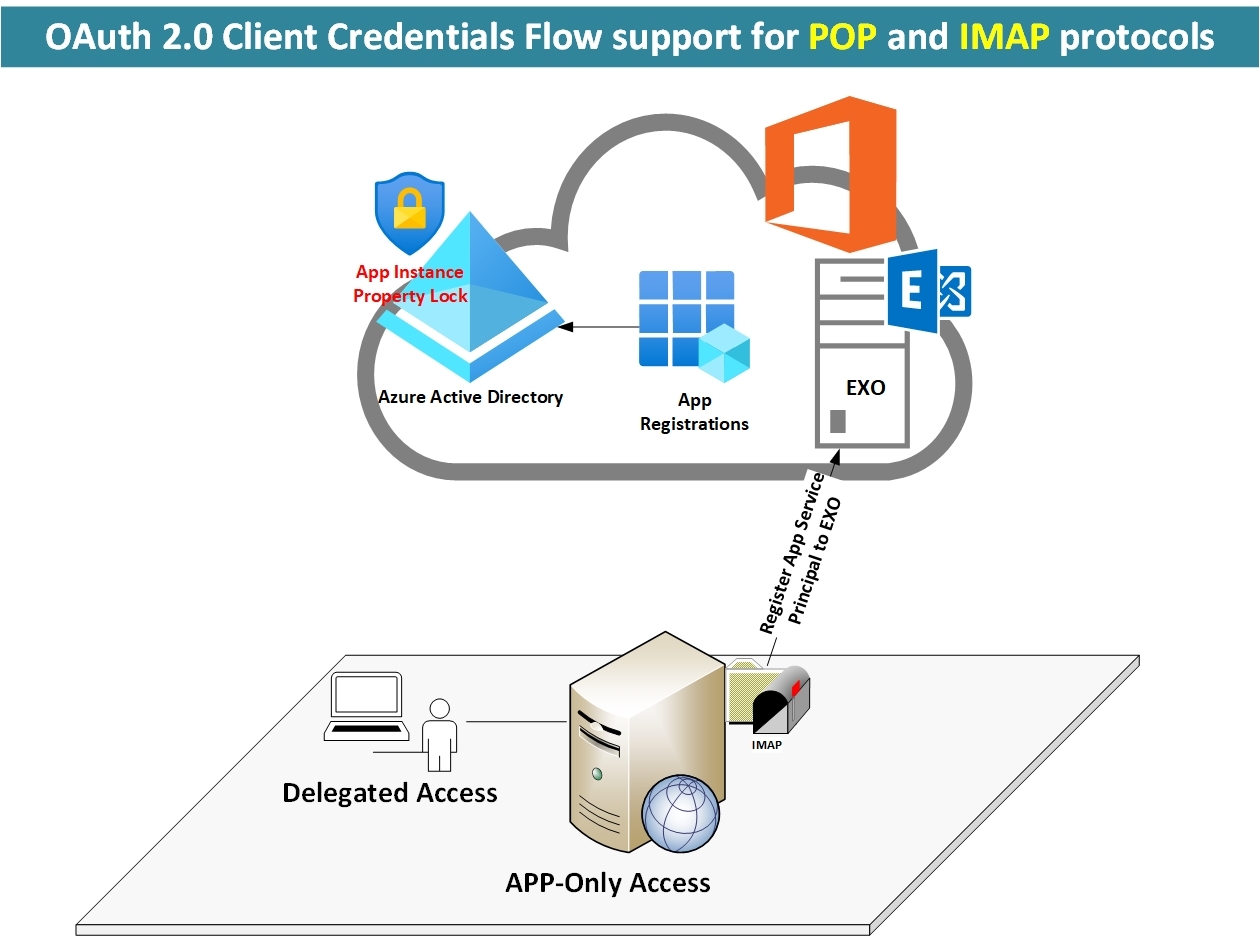
Applications that need to access Exchange Online mailboxes without user interaction and using the identity of the application as opposed to user identity are now supported. This is enabled by using service principals in Exchange and mailbox permissions. While no user interaction is needed, Exchange Online admins will need to provide specific mailbox access (using Exchange Online PowerShell) for applications’ service principals to access the mailboxes.
How it works?
Office 365 tenant admin needs to grant consent to an Azure Active Directory application, then they must register the application’s service principal in Exchange Online. This is done using the new Exchange Online PowerShell.
Go and see yourself what’s difference between Delegated and App Only access.
https://www.linkedin.com/embeds/publishingEmbed.html?articleId=8237710000818296085&li_theme=light
Configure Client App Using OAUTH 2.0 (IMAP)
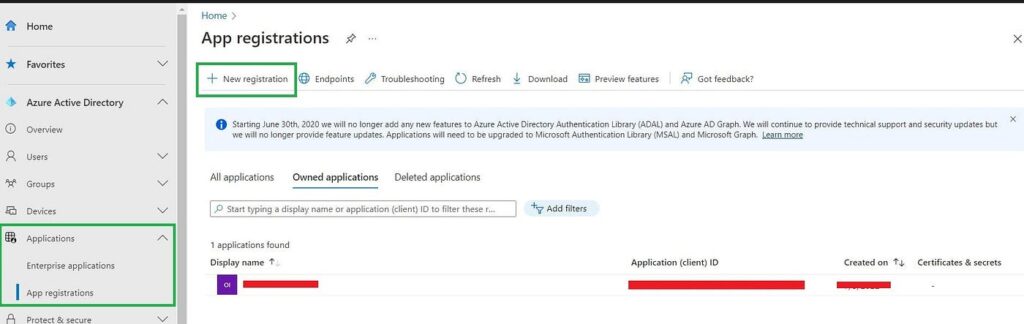
First we need to register Thunderbird App to Azure AD.
- Navigate to Applications -> App Registration
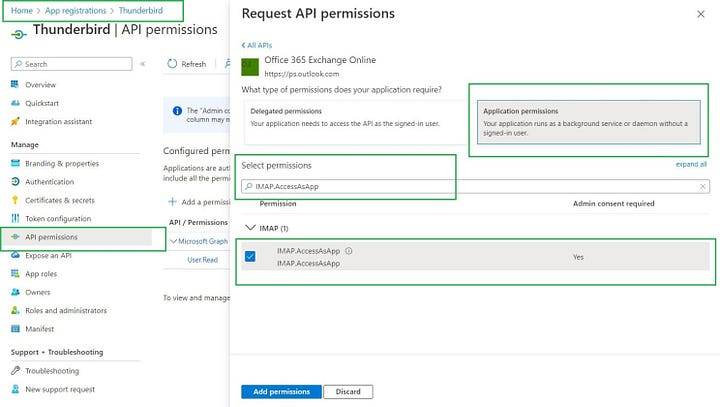
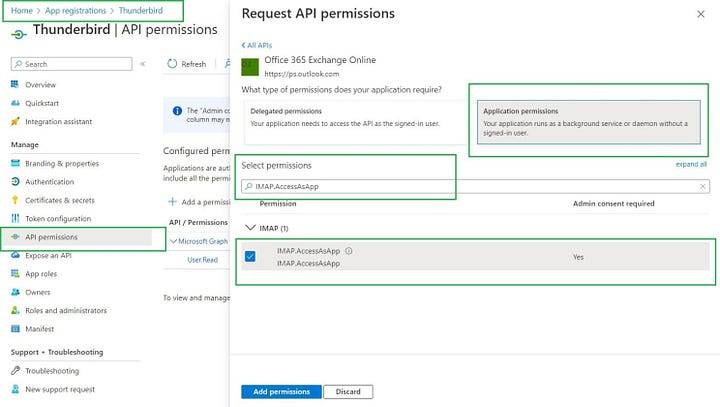
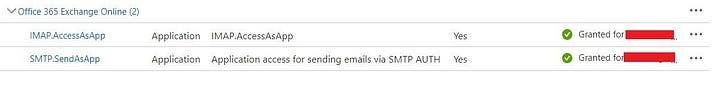
Add the IMAP permissions to Azure AD
- Select the APIs my organization uses tab and search for “Office 365 Exchange Online”.
- Click Application permissions.
For IMAP access, choose the IMAP.AccessAsApp permission.
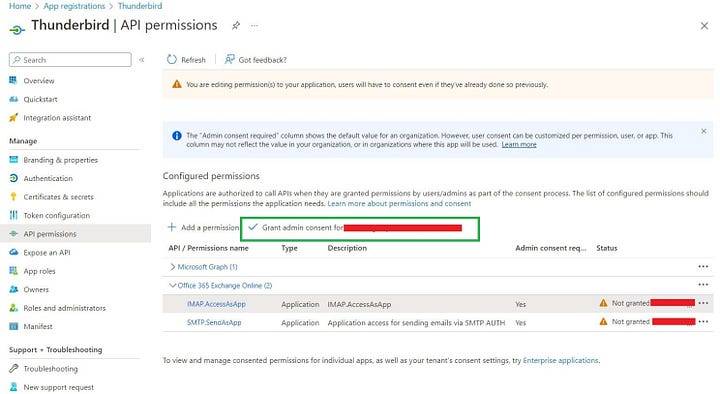
Next we need to grant admin consent.
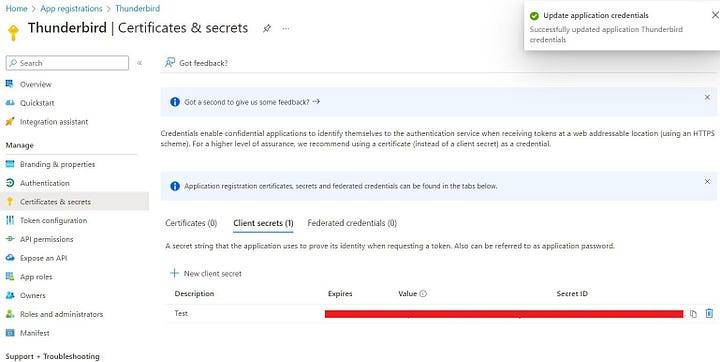
Configure Secret for Client App:
Register service principals in Exchange Online
Once your Azure AD application is consented to by a tenant admin, the tenant admin must register your AAD application’s service principal in Exchange via Exchange Online PowerShell.
New-ServicePrincipal -AppId <APPLICATION_ID> -ServiceId <OBJECT_ID> [-Organization <ORGANIZATION_ID>]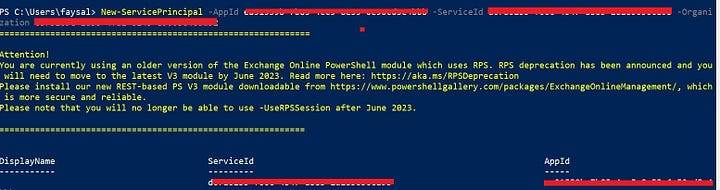
The following is an example of how to give your application’s service principal access to one mailbox:
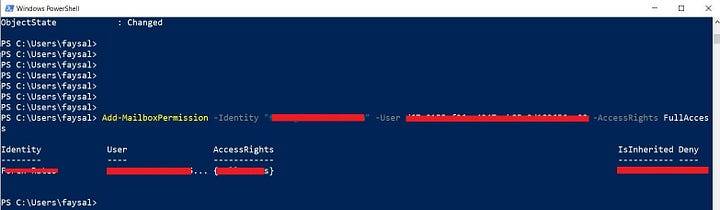
Using the same command you can grant access to shared mailboxes as well.
Finally ! You can use that information in your app or code.
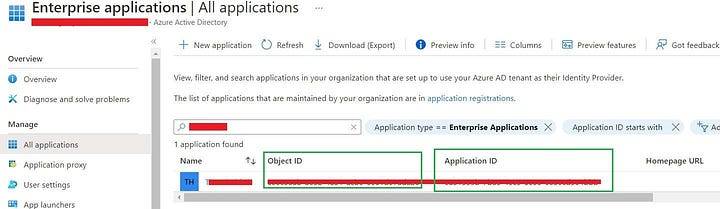
Tip ! Never use Application ID and Object ID form “App Registration” Dashboard, instead use from Enterprise Applications.
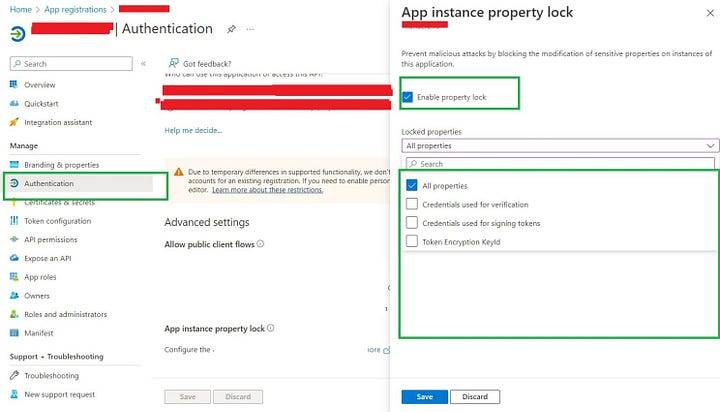
Configure app instance property lock for your applications (Secure Apps from OAuth Hijacking)
Microsoft introduced a new feature called “App Instance Property Lock” to protect OAuth based apps.
https://www.linkedin.com/embeds/publishingEmbed.html?articleId=7741748884255750259&li_theme=light