OAuth 2.0 Client Credentials Flow support for POP
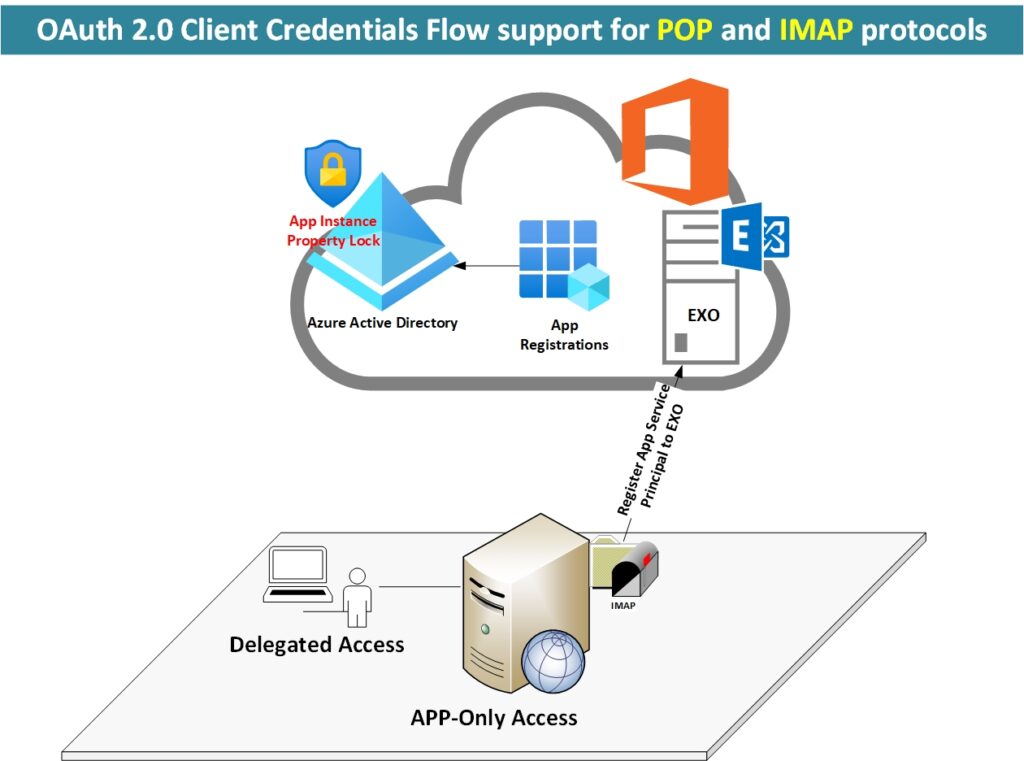
Overview Applications that need to access Exchange Online mailboxes without user interaction and using the identity of the application as opposed to user identity are now supported. This is enabled by using service principals in Exchange and mailbox permissions. While no user interaction is needed, Exchange Online admins will need to provide specific mailbox access […]
Mailbox Migration from Exchange Server 2010 Hybrid with Office 365 to Exchange Server 2016
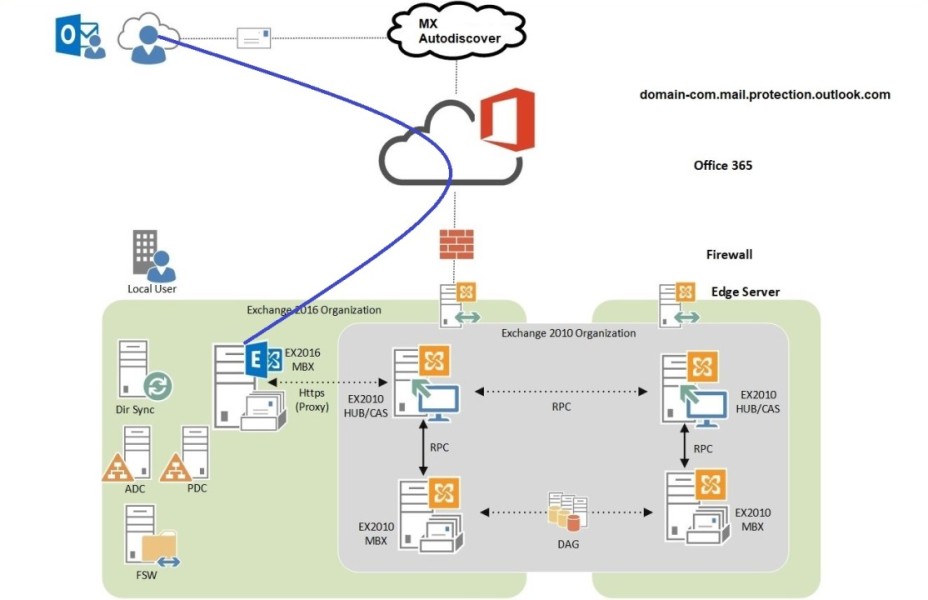
Prerequisites for Coexistence In order to deploy Exchange Server 2016 in the existing organization first we have to make sure that Exchange Server 2010 is ready and prerequisites are satisfied. Installation & Configuration of Prerequisites Exchange Server 2010 required the following prerequisites in order to meet coexistence requirements; Deploying Exchange Server 2016 Installation & Configuration […]
Streamlining your Exchange Server permissions to prevent bad actors from gaining unauthorized access to your organization’s email

Your Data is very important !!! Email servers are gold mine for hackers… Modern day cyber security threats are constantly evolving, making it increasingly difficult for organizations to protect their networks and data from unauthorized access. Some of the most common threats include: To combat these threats, organizations must implement robust security measures, such as firewalls, intrusion […]
Recovering Exchange Server DAG Member Node
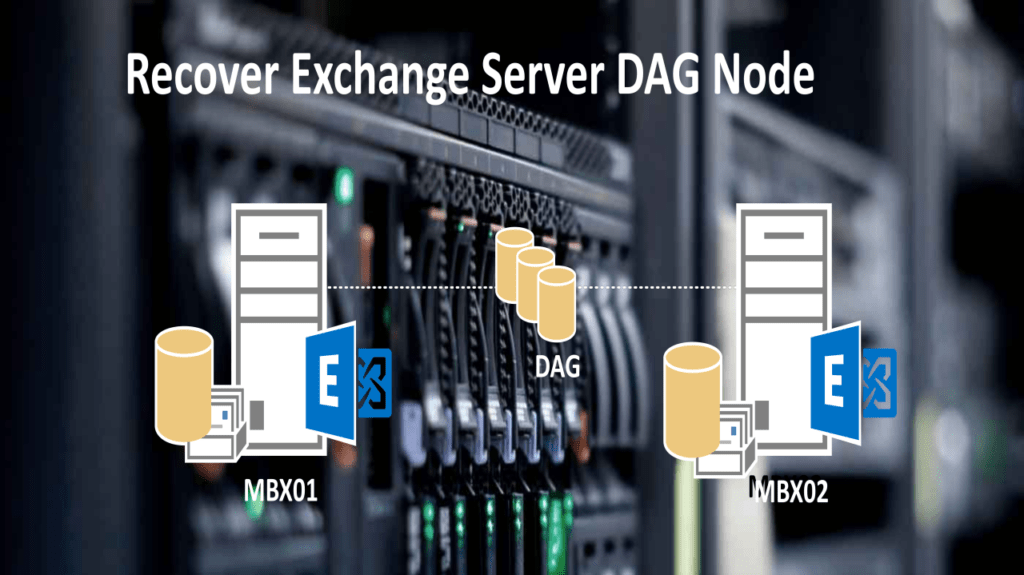
Overview If a Mailbox server that’s a member of a database availability group (DAG) is lost or fails, and is unrecoverable and needs replacement, you can run a server recovery operation. Deployment of Underlying Physical/Virtual Machine & Base Windows Server OS What you need to verify before begin If Exchange is installed in a location […]












